Ncipher security empowers world leading organizations by delivering trust integrity and control to their business critical information and applications.
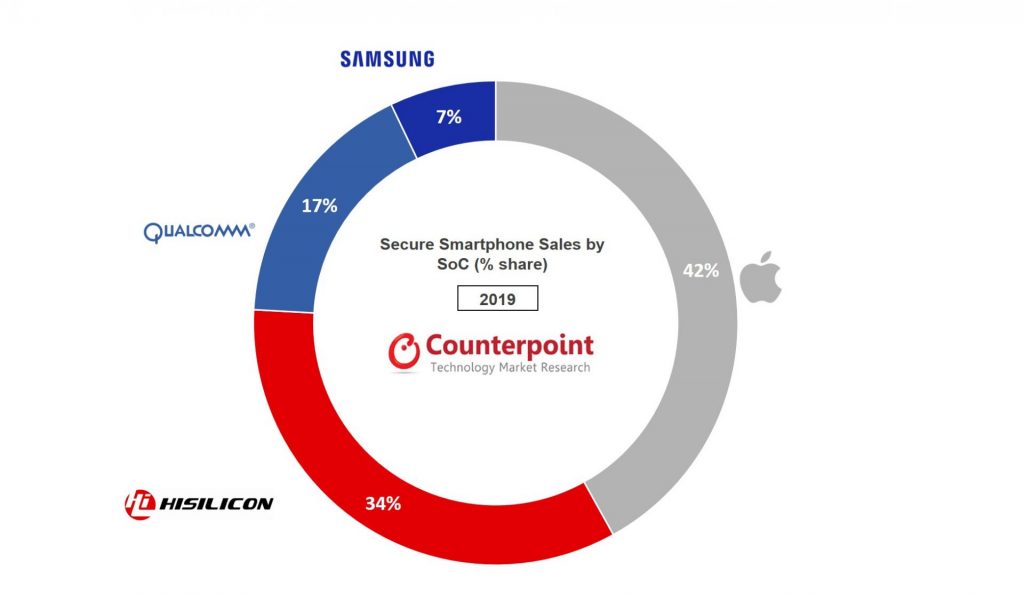
Hardware security module vendors.
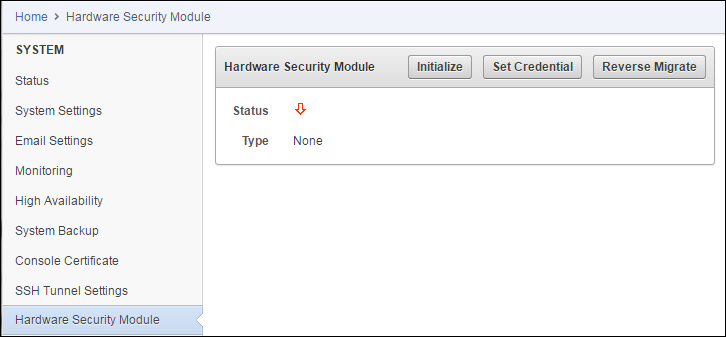
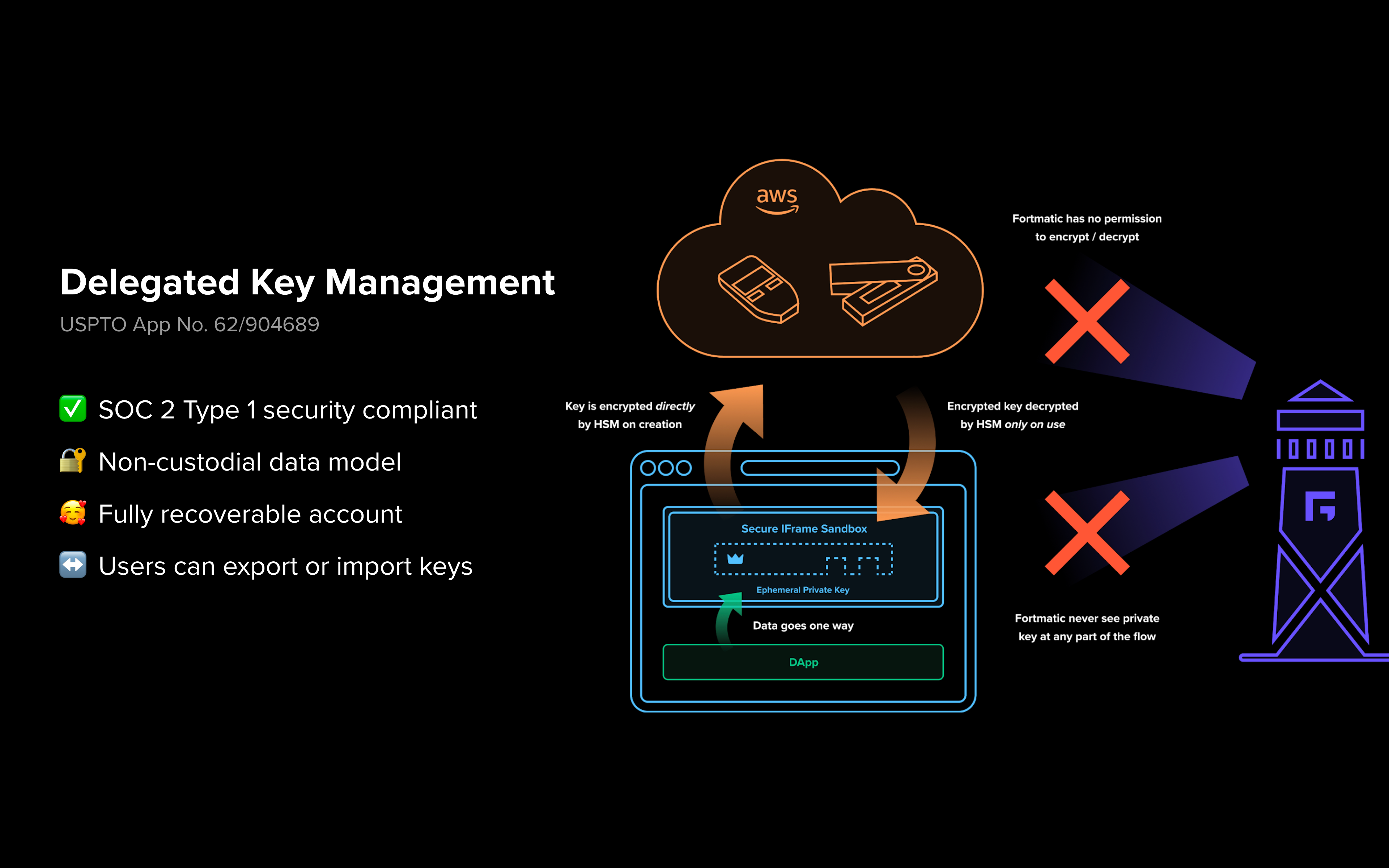
Hardware security modules hsm a hardware security module is a physical computing device that safeguards and manages digital keys for strong authentication and provides cryptoprocessing.
Nshield hardware security modules hsms provide a secure solution for hsm key management generating encryption and signing keys creating digital signatures encrypting data and more.
Hardware security module vendors to no control over hardware and software upgrades.
At pki solutions we work with you to deploy hsms from various manufacturers to enforce defined procedures and ensure integrity and assurance.
A hardware security module or hsm is a dedicated standards compliant cryptographic appliance designed to protect sensitive data in transit in use and at rest through the use of physical security measures logical security controls and strong encryption.
Thales hsms provide a secure crypto foundation as the keys never leave the intrusion resistant tamper evident fips validated appliance.
Utimaco is a world leading manufacturer and specialized vendor of hardware security modules.
Thales hardware security modules provide the highest level of security by always storing cryptographic keys in hardware.
Yet despite these fears the benefits of a more reliable recurring revenue stream single instance implementation and doing away with disruptive upgrade cycles makes the new.